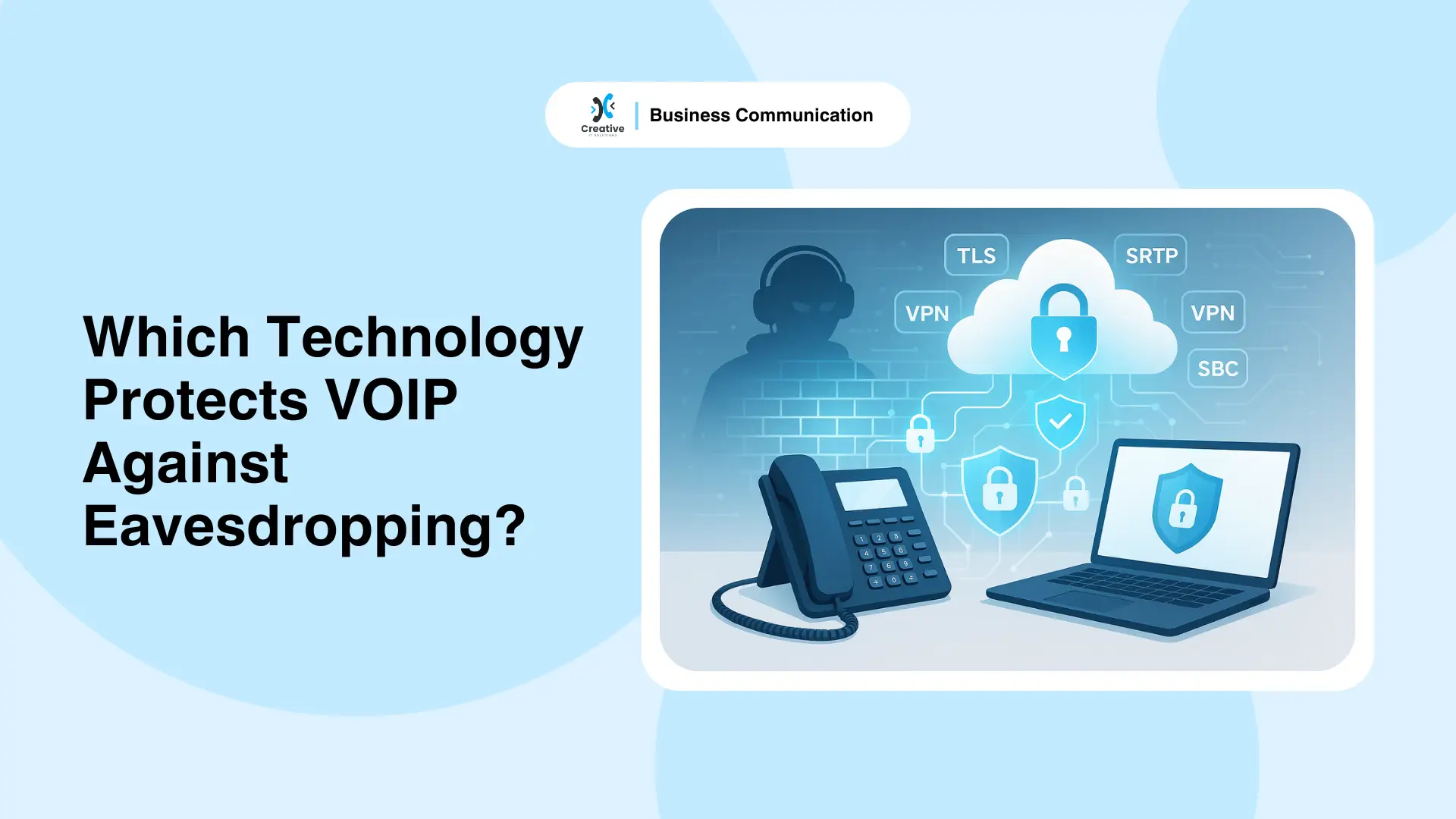
One of the biggest threats to VOIP communication is eavesdropping – when hackers secretly intercept calls to steal sensitive information or monitor conversations. For startups and SMEs in India, this can lead to data leaks, financial fraud, and even loss of customer trust.
Many business owners ask the same question: Which technology protects VOIP against eavesdropping? The answer lies in using a combination of security protocols, encryption methods, and protective tools that keep your calls private and your systems safe.
In this guide, we’ll break down the most effective VOIP security technologies, explain why they matter, and show how Indian businesses can secure their communication with the right approach.
Table of Content
ToggleWhat Is VOIP Eavesdropping and Why It’s a Risk
VOIP Eavesdropping Explained in Simple Terms
VOIP eavesdropping happens when someone secretly listens to your internet-based calls without permission. Just like tapping a landline, hackers can tap into VOIP networks by exploiting weak security. Since VOIP converts voice into digital packets that travel over the internet, unprotected calls can be captured and decoded.
How Hackers Intercept Unencrypted Calls
Hackers use different tricks to access VOIP traffic:
- Unencrypted Calls: If your VOIP system does not use encryption, call data travels like an open postcard – easy for anyone on the network to read.
- Public Wi-Fi Risks: Calls made over unsecured Wi-Fi can be intercepted using packet-sniffing tools.
- Man-in-the-Middle Attacks: Hackers insert themselves between the caller and receiver, capturing call data without either side noticing.
Once they have access, attackers can replay conversations, steal login credentials, or even sell the data.
Real Risks for SMEs: Data Leaks, Fraud, Compliance Issues
For startups and SMEs, the impact of VOIP eavesdropping can be serious:
- Data Leaks: Confidential client or financial details can be exposed.
- Fraud: Hackers can steal sensitive business information or impersonate employees.
- Compliance Issues: Businesses in sectors like finance, healthcare, or legal must meet data protection standards. A single breach can lead to legal penalties and loss of reputation.
Example: An SME in Delhi handling customer payments over VOIP could face financial fraud if hackers intercept card details during a call.
Which Technology Protects VOIP Against Eavesdropping?
When business owners ask, “Which technology protects VOIP against eavesdropping?”, the answer isn’t just one tool – it’s a combination of modern security technologies. Let’s break them down.
Encryption Protocols (TLS, SRTP)
- TLS (Transport Layer Security): Protects the “signaling data” – the information about who is calling whom, when, and how. Without TLS, hackers could track your call setup details.
- SRTP (Secure Real-Time Transport Protocol): Encrypts the actual voice stream, making conversations unreadable to outsiders. Even if attackers capture the data, they can’t decode it.
Example: An SME in Gurgaon using VOIP without SRTP risks having client conversations recorded by attackers on the same network. With SRTP enabled, the call remains private.
Firewalls and Session Border Controllers (SBCs)
- VOIP Firewalls: Designed specifically for internet-based calling, they block suspicious traffic, prevent denial-of-service (DoS) attacks, and stop unauthorized access.
- Session Border Controllers (SBCs): Act as gatekeepers between your VOIP network and the outside world. They prevent call hijacking, toll fraud, and ensure only trusted traffic passes through.
Enterprises often use SBCs for compliance and monitoring. For SMEs, managed firewalls offer affordable but strong protection.
VPNs for VOIP
A Virtual Private Network (VPN) creates a secure tunnel for your VOIP calls. This hides your call traffic from hackers and prevents interception, especially when employees work remotely on public Wi-Fi.
Example: A remote employee in Bangalore making VOIP calls over café Wi-Fi is at risk of eavesdropping. With a VPN, the call data is encrypted and hidden from attackers.
Multi-Layer Security for Enterprises
The strongest protection comes from combining technologies:
- Use TLS + SRTP for call encryption.
- Deploy firewalls or SBCs for traffic filtering.
- Add VPNs for remote workers.
- Train employees to avoid weak passwords and unsafe Wi-Fi.
Multi-layer security ensures that even if one layer is bypassed, others still protect the call.
In short, the best answer to “Which technology protects VOIP against eavesdropping?” is not one tool, but a layered approach. Encryption, firewalls, SBCs, and VPNs together make VOIP communication secure, reliable, and ready for business use.
VOIP Encryption – The First Layer of Protection
When business owners ask how to secure their VOIP calls, the first answer is encryption. Without it, calls are like postcards: anyone on the network can read them. With encryption, calls are scrambled into unreadable data, safe from hackers. Let’s look at the three main types.
Transport Layer Security (TLS)
TLS protects the signaling part of a VOIP call – details like who is calling, when the call starts, and how the session is set up.
- Without TLS: Hackers could see your call logs, numbers dialed, or even reroute calls.
- With TLS: This information is encrypted, keeping your call setup private and tamper-proof.
Think of TLS as sealing the envelope around your call request so no one can peek at the sender and receiver details.
Secure Real-Time Transport Protocol (SRTP)
SRTP protects the actual voice stream – the conversation itself.
- Without SRTP: Hackers using packet-sniffing tools can record and replay your entire conversation.
- With SRTP: The audio data is scrambled using strong encryption, so even if intercepted, it’s meaningless without the decryption key.
For an SME in Delhi handling client payments over VOIP, SRTP ensures that sensitive numbers or discussions cannot be stolen mid-call.
End-to-End VOIP Encryption
End-to-end encryption goes a step further. Instead of just securing parts of the call, it encrypts everything from the caller’s device to the receiver’s device.
- Useful for industries like finance, healthcare, or legal services where calls often contain highly confidential information.
- Prevents even the VOIP provider from accessing the content of your calls.
If your business handles sensitive client data daily, end-to-end VOIP encryption provides the highest level of protection against eavesdropping.
In short, VOIP encryption is the first layer of defense against eavesdropping. TLS secures call setup, SRTP locks down the audio, and end-to-end encryption gives businesses maximum privacy.

Using VPN and Firewalls for VOIP Security
While encryption is the first line of defense, it’s not enough on its own. Businesses also need tools that hide VOIP traffic and block suspicious activity. Two of the most effective technologies for this are VPNs and VOIP firewalls.
Role of VPN in Hiding VOIP Traffic from Hackers
A Virtual Private Network (VPN) creates a secure “tunnel” for your VOIP calls. It hides call traffic from hackers by encrypting everything between your device and the server.
- Without VPN: Calls made over public Wi-Fi or shared office networks are easy targets for attackers.
- With VPN: Hackers can’t see or capture the VOIP traffic, even if they’re on the same network.
Example: An employee in Bangalore using café Wi-Fi to make a client VOIP call could be exposed to eavesdropping. With a VPN, the call data is invisible to anyone on that network.
How VOIP Firewalls Block Suspicious Traffic
A VOIP firewall is built specifically for internet calling. Unlike regular firewalls, it understands VOIP protocols and can filter harmful traffic.
- Blocks denial-of-service (DoS) attacks that overload networks.
- Stops unauthorized connections from reaching your VOIP system.
- Keeps call quality stable by prioritizing safe traffic.
For SMEs in Delhi handling multiple client calls daily, a VOIP firewall ensures that only legitimate traffic gets through, protecting call quality and reducing downtime.
Why SMEs in India Should Consider Managed Firewalls
Not every SME has the technical skills to configure firewalls. That’s where managed firewall services come in:
- Providers monitor your VOIP traffic 24/7.
- Threats are blocked automatically without your team having to act.
- Scales with your business, so you don’t need to invest in heavy hardware.
For growing SMEs, managed firewalls offer enterprise-level VOIP security without the cost of hiring in-house IT staff.
Session Border Controllers (SBCs) – Enterprise-Grade Protection
For businesses that handle a high volume of calls, a Session Border Controller (SBC) is like a digital security guard for your VOIP system. While VPNs and firewalls protect traffic, SBCs go further by controlling, monitoring, and securing every VOIP session that enters or leaves your network.
How SBCs Act as Gatekeepers for VOIP Networks
An SBC sits between your internal VOIP network and the outside world. It:
- Authenticates users before they connect.
- Ensures only safe, approved calls pass through.
- Protects your Private Branch Exchange (PBX) system from outside threats.
Think of an SBC as the reception desk of your VOIP system – it checks IDs, verifies visitors, and blocks anyone suspicious.
Prevent Call Hijacking and Toll Fraud
Without proper security, hackers can hijack VOIP lines to make expensive international calls – a common scam known as toll fraud.
- SBCs detect unusual call patterns, like sudden spikes in international traffic.
- They block or shut down suspicious activity before it costs your business money.
Example: An SME in Delhi with overseas clients can lose thousands in minutes if fraudsters hijack their VOIP line. An SBC stops this before damage occurs.
Extra Layer of Compliance and Monitoring
For industries like finance, healthcare, and BPOs, compliance is critical. SBCs provide:
- Detailed call logs for audits.
- Monitoring tools that track call quality and usage.
- Policy enforcement to ensure calls meet telecom and data security regulations in India.
For a call center in NCR, an SBC not only protects calls but also helps prove compliance during regulatory checks.
In short, SBCs provide enterprise-grade protection by acting as a gatekeeper, fraud detector, and compliance enforcer. For SMEs moving into large-scale VOIP use, adding an SBC ensures safe, reliable, and legally compliant communication.
VOIP Security Best Practices for Businesses
Technology like encryption, firewalls, and SBCs play a big role in VOIP security, but businesses must also follow good practices every day. These small steps make a big difference in protecting your calls from eavesdropping and fraud.
Keep Software and PBX Updated
- Hackers often target outdated VOIP software and PBX systems.
- Always install the latest security patches from your provider.
- Update firmware on VOIP phones and routers regularly.
Example: A Delhi SME using an old PBX without updates left itself open to a known vulnerability that hackers exploited to reroute calls.
Use Strong Passwords and Two-Factor Authentication
Weak or reused passwords are easy to crack.
- Set long, unique passwords for all VOIP accounts.
- Enable two-factor authentication (2FA) so even if a password is stolen, hackers can’t log in without the second code.
This is especially important for admin accounts that manage call routing and billing.
Monitor Traffic for Unusual Patterns
Unusual call behavior often signals an attack.
- Use monitoring tools or dashboards to spot sudden spikes in call volume.
- Watch for unexpected international calls or traffic outside business hours.
Example: A sudden burst of calls to overseas numbers could mean toll fraud – quick monitoring can stop it in minutes.
Train Staff on Safe Call Practices
Employees are often the weakest link in VOIP security.
- Teach them to avoid using public Wi-Fi for business calls without VPN.
- Remind them never to share login credentials or call details casually.
- Conduct short awareness sessions on common scams like phishing calls.
Even the best technology won’t help if your team isn’t trained to use VOIP securely.
In short, VOIP security is a mix of strong technology and smart daily habits. By keeping systems updated, using strong passwords, monitoring traffic, and training staff, SMEs can reduce risks and keep customer communication safe.
VOIP Security in India – What Businesses Must Know
When it comes to VOIP security, Indian businesses have unique challenges. It’s not just about technology – compliance with telecom rules is equally important. Ignoring these can lead to penalties, service disruptions, or even legal issues.
Indian Compliance Rules for VOIP Security
In India, VOIP services are regulated by the Department of Telecommunications (DoT) and must follow strict guidelines:
- Only licensed VOIP providers can legally issue numbers and manage VOIP traffic.
- KYC verification (Aadhaar, PAN, GST, or CIN for businesses) is mandatory before activation.
- Unauthorized VOIP gateways or international calling without licenses are considered illegal.
For SMEs, this means always working with a licensed provider instead of setting up unsecured or DIY VOIP systems.
Why SMEs in Delhi NCR and All Over India Are Investing in Secure Cloud Telephony
The Delhi NCR region is home to thousands of startups, IT companies, and BPOs that rely heavily on customer calls. These businesses face:
- Data sensitivity: Handling client financial or personal details.
- High call volumes: Customer support and sales teams depend on clear, reliable connections.
- Compliance needs: Many SMEs serve overseas clients who demand strong data protection.
As a result, more SMEs are moving from basic VOIP setups to secure cloud telephony systems that combine encryption, firewalls, monitoring, and compliance support.
Work with a Trusted VOIP Service Provider in Delhi NCR
If your business depends on VOIP communication, don’t leave security to chance. Partner with a licensed, reliable VOIP service provider in Delhi NCR to ensure your calls are encrypted, compliant, and backed by 24/7 support.
VOIP security in India is not optional – it’s a must. By choosing licensed providers and investing in secure cloud telephony, SMEs protect their customers, avoid legal risks, and build long-term trust.
Want secure and reliable VOIP for your business?
Explore our Cloud Telephony services at Creative IT Solutions and discover how a trusted VOIP service provider in Delhi NCR can protect your calls, reduce costs, and scale with your growth.
Frequently Asked Questions
Q1. Which technology can be used to protect VOIP against eavesdropping?
The best technologies include encryption (TLS and SRTP), VOIP firewalls, Session Border Controllers (SBCs), and VPNs. Together, they prevent hackers from listening to your calls.
Q2. Which of the following should be used to secure VOIP communications against eavesdropping?
Businesses should use TLS for signaling, SRTP for voice encryption, and VPNs for remote access. Adding SBCs and managed firewalls gives enterprise-grade protection.
Q3. What is the most secure security measure to protect against eavesdropping?
The most secure measure is end-to-end VOIP encryption, where calls are encrypted from one device to the other, making it impossible for anyone – even providers – to intercept.
Q4. Which protocol protects the contents of a VOIP conversation from eavesdropping?
The Secure Real-Time Transport Protocol (SRTP) protects the actual audio stream in VOIP calls, ensuring conversations remain private even if intercepted.
Q5. Which technology does VOIP use?
VOIP uses Voice over Internet Protocol to transmit voice as digital data packets over the internet instead of traditional copper phone lines.
Q6. What technique is commonly used to protect transmitted data against eavesdropping?
The most common technique is data encryption, where call data is scrambled into unreadable packets. In VOIP, this is done using TLS and SRTP.
7. What is VOIP security?
VOIP security refers to the tools, technologies, and best practices used to protect internet-based calls from threats like eavesdropping, call hijacking, and fraud.
8. Why is VOIP security important for businesses in India?
Without VOIP security, businesses risk data leaks, financial fraud, and compliance violations. For SMEs in India, secure VOIP ensures reliable communication and customer trust.